2026 won’t be a year where more security tools automatically mean more security. It’s no longer about individual products, but about customer-centered solutions that make the difference. Providers will succeed when they act as true service partners offering real value.
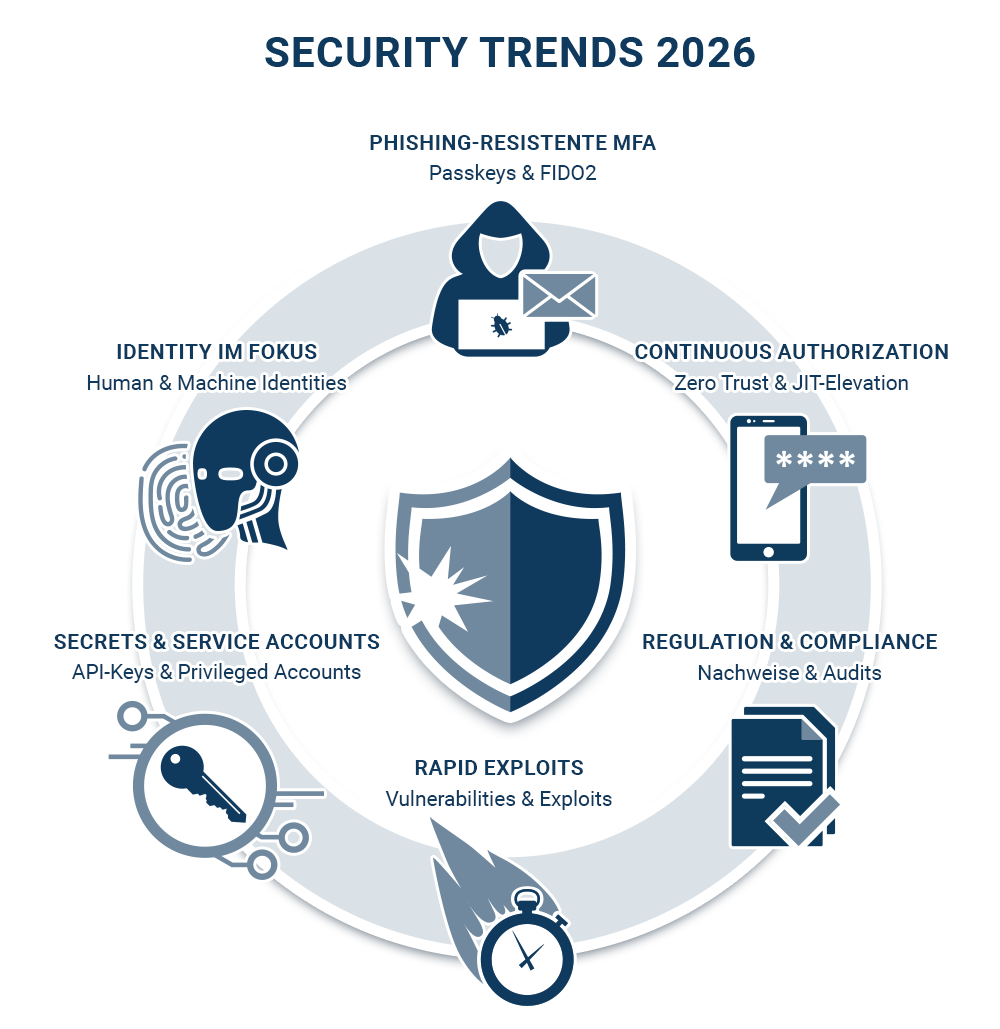
Identity has now fully replaced the network as the primary attack surface. Attackers no longer need to break in — they simply log in. At the same time, AI-driven attacks, rapidly exploited vulnerabilities, and complex EU regulations (such as NIS2 and DORA) are increasing pressure on CISOs, IT, and compliance leaders. The common denominator: Identity & Access Management (IAM) has become the central control lever for risk reduction, accountability, and resilience.
Identity Becomes the Main Attack Surface
The strongest signals in incident response and threat reports remain consistent: stolen or guessed credentials, phishing/pretexting, and identity abuse continue to rank among the most common entry points for security incidents. The Verizon Data Breach Investigations Report 2025 highlights compromised credentials, exploited vulnerabilities, and phishing as key patterns.
What’s new in 2026 is the growing diversity of identities:
- Machine and workload identities (cloud workloads, containers, service principals)
- API and token identities (long-lived tokens, session tokens)
- Privileged identities (admin, break-glass, third-party)
- AI identities / agent-based access: autonomous systems and agents that appear to access data and systems legitimately
Strong market investment underscores this trend — for example, CrowdStrike’s recent acquisition of an identity security firm to enhance continuous identity and real-time decision-making for human, machine, and AI identities.
What this means for decision-makers: IAM is no longer just an IT operation — it’s the backbone of cyber defense. Those who don’t master identities, permissions, tokens, and sessions will lose.
Phishing-Resistant MFA & Passkeys: 2026 Marks the Year of Full Transition
MFA is not all the same. Attacks such as MFA fatigue, token theft, and session hijacking have shown that traditional factors are no longer enough. The shift is moving toward:
- Phishing-resistant MFA (e.g., FIDO2/WebAuthn)
- Passkeys as user-friendly standards for strong authentication
- Conditional access based on risk, device posture, and geography
Microsoft’s Digital Defense Report emphasizes the effectiveness of stronger, multilayered identity protection against widespread password attacks.
So where should 2026’s practical focus lie?
- Implement passkeys and phishing-resistant MFA first for admins, remote access, and email/collaboration
- Then expand step by step to standard users — supported by a well-planned adoption strategy (support, rollout, recovery)
Continuous Authorization Instead of Login = Trust
The traditional model — log in once and you’re good to go — no longer fits the realities of cloud environments, APIs, and AI agents. The trend is moving toward continuous authorization:
- Just-in-Time (JIT) Privileges: Granting access only when and for as long as needed
- Just-Enough-Access (JEA): Limiting permissions to the absolute minimum required
- Session Monitoring & Step-up Authentication: Adjusting authentication dynamically when risk levels change
- Identity Threat Detection & Response (ITDR): Detecting and stopping identity attacks across the entire chain (IdP, MFA, token, directory)
This is where Security and IAM seamlessly converge: IAM defines the policy, Security provides the telemetry — together enabling real-time control.
Vulnerability Exploitation Is Accelerating
The window between vulnerability disclosure and active exploitation continues to shrink. Why this matters for IAM: patching remains essential, but IAM determines whether a successful exploit turns into a catastrophe or stays a contained incident.
Non-Human Identities & Secrets: The Hidden Blind Spot
One of the most costly trends of 2026 involves compromised service accounts, API keys, certificates, and secrets. The reasons include long validity periods, unclear ownership, excessive permissions, and insufficient rotation or discovery.
Mandiant highlights that many cloud compromises stem from identity and policy gaps or misconfigurations extending well beyond traditional network perimeters.
What CISOs and IT leaders should prioritize now:
- Inventory of all non-human identities (including shadow workloads)
- Automated secrets management and rotation
- Least-privilege reviews for service principals and workloads
- Monitoring for token misuse, unusual grants, and consent attacks
Few organizations truly know how many non-human identities (NHIs) are operating uncontrolled within their systems. With OEDIV’s NHI Inventory, you gain a full overview of all certificates and SSH keys within just six days — including a clear risk assessment based on current security standards and actionable recommendations for compliance and automation.
The result: 100% transparency, reduced risk, and a clear roadmap toward effective identity governance.
Compliance 2026: Proof of Control Is as Crucial as Protection Itself
With NIS2, requirements for cybersecurity risk management measures are increasing. In parallel, the financial sector and its ICT providers face DORA, emphasizing resilience, testing, and third-party management.
For compliance officers, this means: IAM becomes the audit backbone, generating the evidence needed to answer key questions such as:
- Who had access, when, and to what? (permissions, groups, roles)
- Were privileged actions properly monitored? (PAM, session logging)
- Are policies effectively enforced? (conditional access, MFA coverage)
- Is the joiner/mover/leaver process handled cleanly? (IGA, recertification)
AI in the SOC – and AI on the Attacker Side: Agentic Security Needs Guardrails
Security teams are planning greater use of AI and automation in 2026. Yet, the more autonomous systems act, the more essential it becomes that every automation is governed by strong identity controls — defining who or what can do what, within what scope, how access is revoked, and how it’s monitored.
Practical IAM guardrails for AI and agents include:
- Separate, tightly scoped identities per agent or use case
- JIT tokens with short lifetimes, no long-lived secrets
- Approval workflows for high-risk actions
- Full logging and anomaly detection
Our Conclusion
The cybersecurity trends of 2026 converge on one message: those who control identities, entitlements, and sessions control the risk. IAM is no longer just about authentication — it’s an operational model encompassing governance (IGA), privilege management (PAM), continuous authorization, non-human identity protection, and measurable auditability for NIS2 and DORA compliance.
To reduce risk amid growing complexity in 2026, organizations should start with:
- IAM maturity and risk assessments (including non-human identities)
- Roadmaps for passkeys and phishing-resistant MFA
- PAM/IGA programs with measurable controls and audit evidence
- ITDR use cases that stop identity attacks early
Above all, it pays to work with an experienced cybersecurity partner who acts as a true service provider, focusing on pragmatic, field-tested solutions. Together, digital security can become a real competitive advantage — through scalable zero-trust models, clear identities, and a strong security culture.
Contact:
Waldemar Ahrend-Reimche
CEO,
OEDIV SecuSys GmbH, Rostock
Patrick Piotrowski
Senior Business Consultant IAM
and Sales Representative,
OEDIV SecuSys GmbH, Rostock

