Identity Governance becomes a Security-Critical Foundation
By 2026, Identity Governance & Administration (IGA) will be at the core of enterprise security. The increasing complexity of hybrid IT landscapes, the digitalisation of business-critical processes and the growing number of human and non-human identities make modern, auditable access management essential. Regulatory frameworks designed to strengthen digital resilience, such as NIS-2 and DORA, intensify these requirements, placing IGA at the heart of governance, risk and compliance (GRC), especially for operators of critical infrastructures (KRITIS).
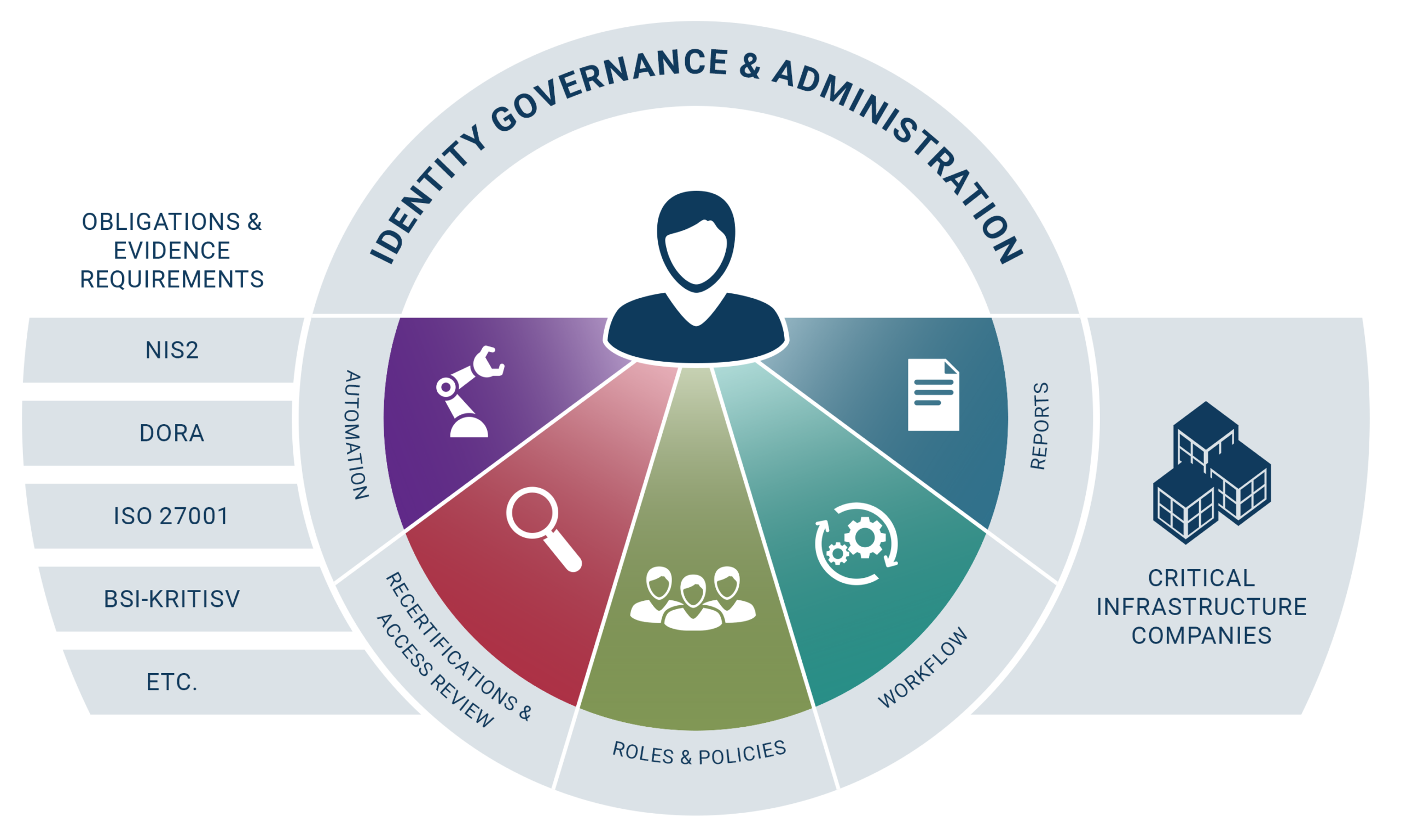
Regulatory Pressure: NIS-2 Fundamentally Changes the Requirements
With NIS-2, the EU has significantly tightened cybersecurity expectations. The directive expands the range of obligated entities and mandates systematic risk management, strict access controls, and clear executive-level accountability. Identity and permission processes must be demonstrably secure and fully documented. Furthermore, the introduction of stricter reporting obligations and substantial fines increases the pressure on organisations to ensure that their identity governance processes are efficient and compliant. For KRITIS companies, these demands are even more pronounced in the context of the German IT Security Act (BSI-Gesetz), KRITIS regulations and sector-specific security standards.
DORA in the Financial Sector: Digital resilience starts with identities.
In force since January 2025, the Digital Operational Resilience Act (DORA) pursues a similar goal—for banks, insurers, and financial service providers. DORA considers identities a core component of ICT risk management and requires clearly defined, tested, and documented processes for managing digital resilience. Outsourced IT service providers and cloud vendors play a particularly critical role, as their involvement in identity management increasingly affects security.
While NIS-2 and DORA target different sectors, structurally they demand the same: robust, automated, and auditable Identity Governance across all systems and service providers.
IGA at the Heart of modern Identity Security
The market is evolving rapidly: IGA is transforming from a traditional access management tool into the strategic backbone of identity security. Zero-trust frameworks are gaining traction, identity is replacing the network as the primary security perimeter, and the number of non-human identities—such as IoT devices, APIs, and AI agents—is skyrocketing. Companies need clear role models, automated workflows, and continuous controls to securely manage this diversity.
At the same time, IGA, Privileged Access Management (PAM), and Cloud Infrastructure Entitlement Management (CIEM) are increasingly merging into unified platforms. AI-driven analytics helps identify risky permissions, unusual access patterns, and outdated roles at an early stage.
Automation as the Key to Compliance and Efficiency
In order to efficiently meet rising regulatory demands, it is essential to automate identity lifecycle processes. This should include every stage, from employee onboarding and internal role changes to offboarding — the joiner-mover-leaver process. This reduces errors, minimises manual effort and eliminates orphaned accounts. Self-service portals are also becoming increasingly important, as they enable business departments to request and view permissions quickly and systematically. Recertifications are triggered automatically and documented in an audit-proof manner, supporting efficient audits and compliance with BSI or supervisory authority requirements.
Standard interfaces, templates and best practice models also reduce implementation times, which is a key advantage in complex KRITIS environments.

KRITIS under pressure: Attacks, Audits and Increased Executive Accountability
The coming years will present particular challenges for operators of critical infrastructures. Threat levels continue to rise in both IT and operational technology (OT). Attacks on utilities, waterworks and energy infrastructure are becoming more frequent and sophisticated. At the same time, supervisory and auditing bodies are intensifying their scrutiny of approval workflows, access systems, recertifications and incident response capabilities. Management is personally accountable for ensuring the effectiveness of identity-related security measures.
Companies must therefore assess their level of maturity, consolidate siloed solutions, and establish an integrated identity security ecosystem that combines IAM, IGA, PAM and cloud security.
OEDIV SecuSys: Industry Expertise and Technical Excellence
In this demanding environment, choosing the right partner is paramount. OEDIV SecuSys GmbH has over two decades of experience in identity and access management and possesses in-depth technical and industry expertise, even in the KRITIS segment.
Conclusion: 2026 becomes a pivotal year for identity governance
2026 will be a turning point for organisations that take identity governance seriously.
Those that implement modern, automated and strategically embedded IGA frameworks now will lay the foundation for digital resilience, stronger security and long-term compliance. For KRITIS operators, this is synonymous with ensuring operational continuity and regulatory compliance.
Contact:
Waldemar Ahrend-Reimche
CEO,
OEDIV SecuSys GmbH, Rostock
Patrick Piotrowski
Senior Business Consultant IAM
and Sales Representative,
OEDIV SecuSys GmbH, Rostock
With an experienced industry partner like OEDIV SecuSys, organizations can not only meet these challenges but turn identity governance into a strategic advantage for the future.

